The Netherlands is continuously looking into ways to improve the traffic not only for cars but also for cyclists, especially as the number of those owning a bike in the country is impressive, to say the least.
According to 2018 data provided by the government, there were 23 million bicycles in the country for a population of just 17 million people.
As a result, over 10 municipalities in the Netherlands have recently embraced a connected platform that allows smartphones to send information to traffic lights in an attempt to improve the traffic flow and reduce the time waiting for the green light.
More specifically, the system can determine if a group of cars or bicycles is approaching the traffic light and depending on a series of factors, it can determine whether it needs to turn to green.
And while the whole concept is based on a mobile app running on smartphones, white hat hackers Wesley Neelen and Rik van Duijn have demonstrated that such an approach can easily be abused to trick a traffic light to turn green instantly.
“We have looked at these innovations to see if these systems could be manipulated and how manipulation could benefit an attacker. Specifically, we found a way in two different platforms, that allows us to successfully fake a continuous flow of bicyclists that turns the cyclist traffic light instantly green or decreases the time to green,” the hackers explained.
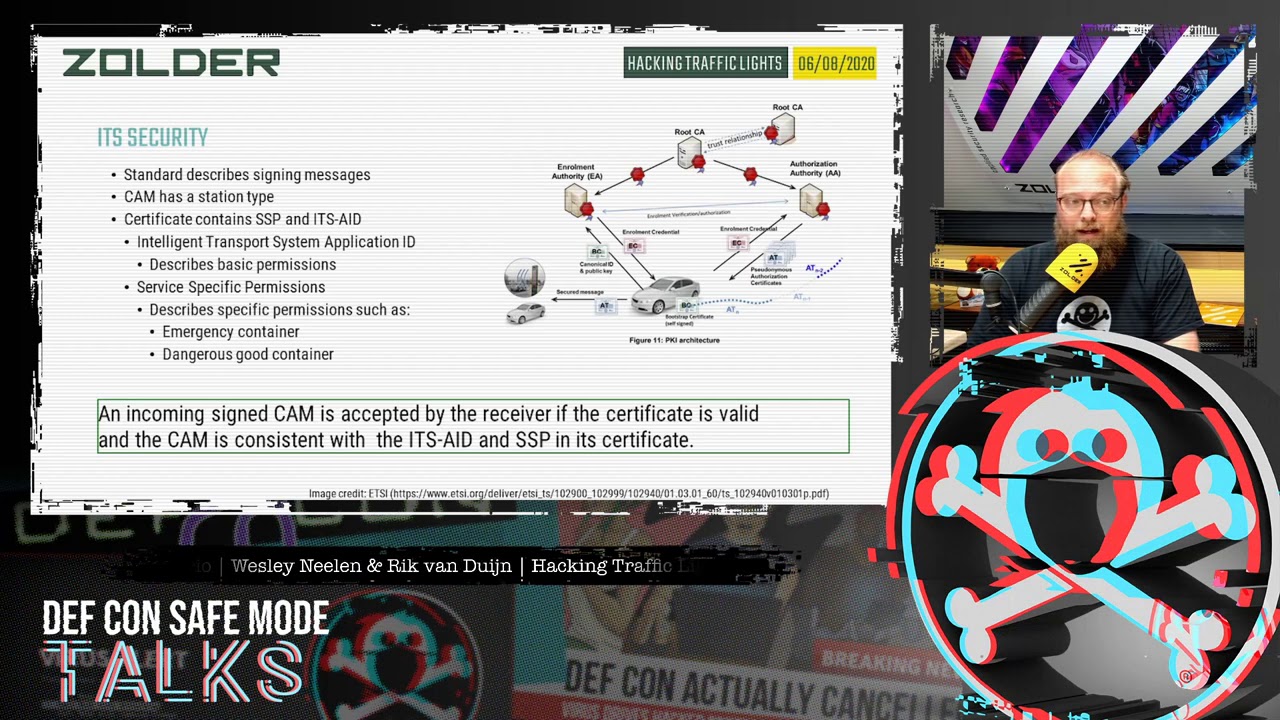
More specifically, the hackers discovered there’s no signing that the app uses, which means that a malicious person can remotely influence a cycling traffic light. The good news is that only the bike indicators are exposed, it seems, with the safety systems remaining intact, which means not all traffic lights can turn green at the same time.
Fixing the whole thing shouldn’t be difficult for authorities in the Netherlands, as the hackers recommend them to implement some form of authentication, monitor unexpected behavior at the backend, and block any attempt to abuse the system from the very early stages.
As a result, over 10 municipalities in the Netherlands have recently embraced a connected platform that allows smartphones to send information to traffic lights in an attempt to improve the traffic flow and reduce the time waiting for the green light.
More specifically, the system can determine if a group of cars or bicycles is approaching the traffic light and depending on a series of factors, it can determine whether it needs to turn to green.
And while the whole concept is based on a mobile app running on smartphones, white hat hackers Wesley Neelen and Rik van Duijn have demonstrated that such an approach can easily be abused to trick a traffic light to turn green instantly.
“We have looked at these innovations to see if these systems could be manipulated and how manipulation could benefit an attacker. Specifically, we found a way in two different platforms, that allows us to successfully fake a continuous flow of bicyclists that turns the cyclist traffic light instantly green or decreases the time to green,” the hackers explained.
More specifically, the hackers discovered there’s no signing that the app uses, which means that a malicious person can remotely influence a cycling traffic light. The good news is that only the bike indicators are exposed, it seems, with the safety systems remaining intact, which means not all traffic lights can turn green at the same time.
Fixing the whole thing shouldn’t be difficult for authorities in the Netherlands, as the hackers recommend them to implement some form of authentication, monitor unexpected behavior at the backend, and block any attempt to abuse the system from the very early stages.